Fine grained audit
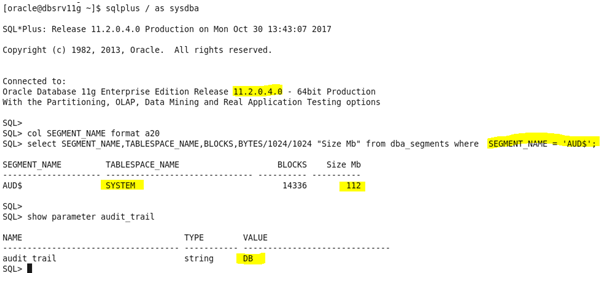
Feature introduced from the RDBMS 9i release. Fine grained auditing extends Oracle existing auditing capabilities. Main features: – Regular auditing must be enabled using the parameter AUDIT_TRAIL. FGA does not require any parameter change . – Sql bind variables are captured by default in FGA – In FGA auditing is more flexible when certain columns are accessed, when a certain condition is considered true. – FGA can be temporarily disabled and enabled. Once identified schema and tables to check we set the policy audit. Suppose you want to control all access to the table ETICA and all operation sql that...